diff options
| author | uvok cheetah | 2023-07-02 20:54:16 +0200 |
|---|---|---|
| committer | uvok cheetah | 2023-07-02 20:54:16 +0200 |
| commit | b8344ef7d419a96a3164e9a827ad4c2eb6145571 (patch) | |
| tree | 1978083330ed663b91ca522b034b9bb31862e59c | |
| parent | b78efd5b78d8da881d12d17a1f8e386f3844c250 (diff) | |
Add post about Wireguard troubles
| -rw-r--r-- | _posts/2023-07-02-shoot-foot-wireguard.md | 82 |
1 files changed, 82 insertions, 0 deletions
diff --git a/_posts/2023-07-02-shoot-foot-wireguard.md b/_posts/2023-07-02-shoot-foot-wireguard.md new file mode 100644 index 0000000..be9de7d --- /dev/null +++ b/_posts/2023-07-02-shoot-foot-wireguard.md @@ -0,0 +1,82 @@ +--- +layout: post +title: Shooting yourself into the foot with Wireguard +date: 2023-07-02 20:11 +0200 +lang: en +categories: tech +--- + +Sunday afternoon. I'm sitting somewhere outside away from home. +Suddenly I remember I forgot to switch my roomba on. Ugh. +But no worries, I got a Wireguard connection set up, so I can +connect to home and switch it on from there. + +Hm. Unfortunately I can't connect to my home router (OpenWRT). Did the dynamic DNS address fail +to update again? Now that I think about it, I can't remember I actually I ever +tested the connection. I tested the connection once when my OpenWRT router was still +running in a VM. Maybe I forgot to set up some things? + +[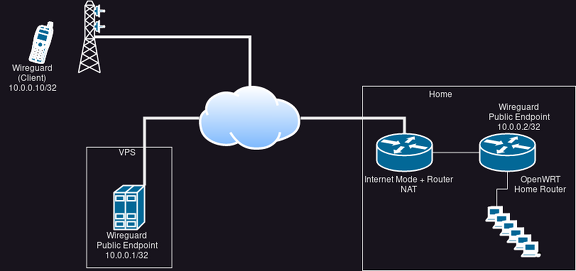](https://pics.uvokchee.de/upload/2023/07/02/20230702201107-0ecdfc52.png) + +But hey, no worries, I'll simply connect to my VPS, and let the Wireguard +routing do its job. Just move the `AllowedIP=0.0.0.0/24` +setting from the OpenWRT endpoint to the VPS endpoint +on the smartphone. + +I can ping my VPS' Wireguard address, but unfortunately, +pings to my OpenWRT "do nothing". +ping doesn't show any output, simply seems stuck. Weird. + +Well, okay, I after I finished enjoying the outsides, I went home +to try to figure out what went wrong. + +Well, lets see, what are the AllowedIPs... + +[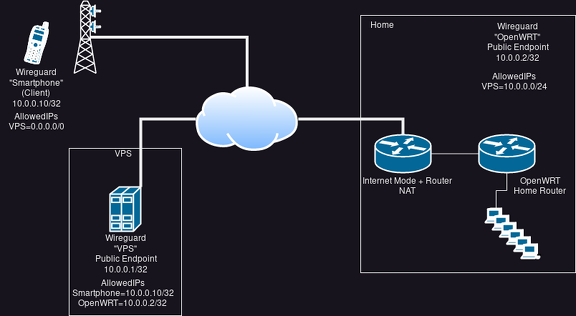](https://pics.uvokchee.de/upload/2023/07/02/20230702201107-5df12e17.png) + +Hm. Seems good enough. +The smartphone pings to the VPS get answered all right. The AllowedIPs match there. +On the VPS via SSH, I can..... not ping my OpenWRT router. Hm. + +Ugh, oh yeah! NAT. Let's edit the Wireguard config on OpenWRT to send `KeepAlive` +packages. Also, I noticed I didn't set a firewall `INPUT` rule in OpenWRT to +allow packages from the upstream router to the Wireguard port. Let's fix that. +(That makes the `KeepAlive` unnecessary technically. *However*, I want to avoid +possible dynamic DNS problems as well. So let my OpenWRT just regularly send a keep-alive). + +So let's test again... +ping from Smartphone to VPS work. ping from VPS to OpenWRT work. + +ping from Smartphone to OpenWRT... Still stuck. The heck? + +Okay, let's see the configs again. Very carefully. + +[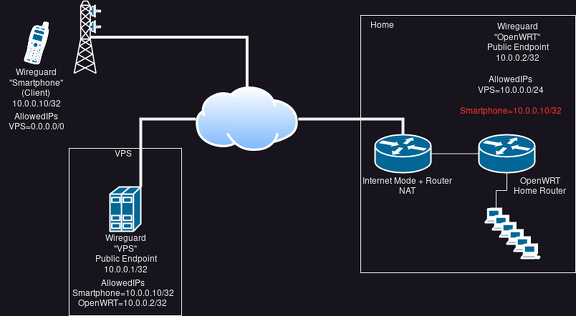](https://pics.uvokchee.de/upload/2023/07/02/20230702201107-597a7b3d.png) + +Well, oops. I still had the smartphone set up as a possible client on OpenWRT. +Apparently, the ping from my smartphone went through my VPS to OpenWRT just fine +It was just... when trying to send the ping reply, OpenWRT / Wireguard found the `AllowedIP` +setting for the smartphone and probably tried to send the reply directly. +Which isn't possible, since the smartphone naturally has no endpoint address set. +(And no, there was no routing entry for the smartphone itself). + +So, to test if this is the problem, I removed the `AllowedIP` setting from the +smartphone on the OpenWRT config. And... the ping works. + +I can't keep it like that, though. So... I added back the `AllowedIP` +setting to the smartphone, and instead modified the config +on Wireguard for Android. Let everything Wireguard-internal +route via OpenWRT. +(Reminder: longest prefix wins. `/24` is longer than `/0`). + +[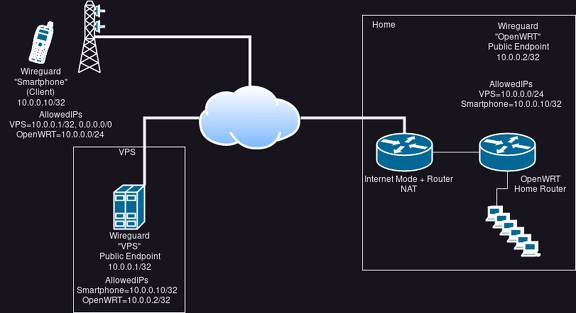](https://pics.uvokchee.de/upload/2023/07/02/20230702203947-9169ae4a.png) + +Et voilá! ping still works. + +Only... I still couldn't start my roomba. No wonder, OpenWRT was configured not to allow +any `FORWARD`ing from the Wireguard zone. +(Masquerading on the Wireguard zone was already enabled by the way.) +So, after adding the zone with my roomba +to the list the Wireguard zone is allowed to forward to, I could reach my roomba as well. + +All is good... Until the next time something breaks. |
